UCD Digital Forensics Investigation Research (DigitalFIRE) Laboratory
-
Introduction to CS and IT for Digital Forensics Professionals
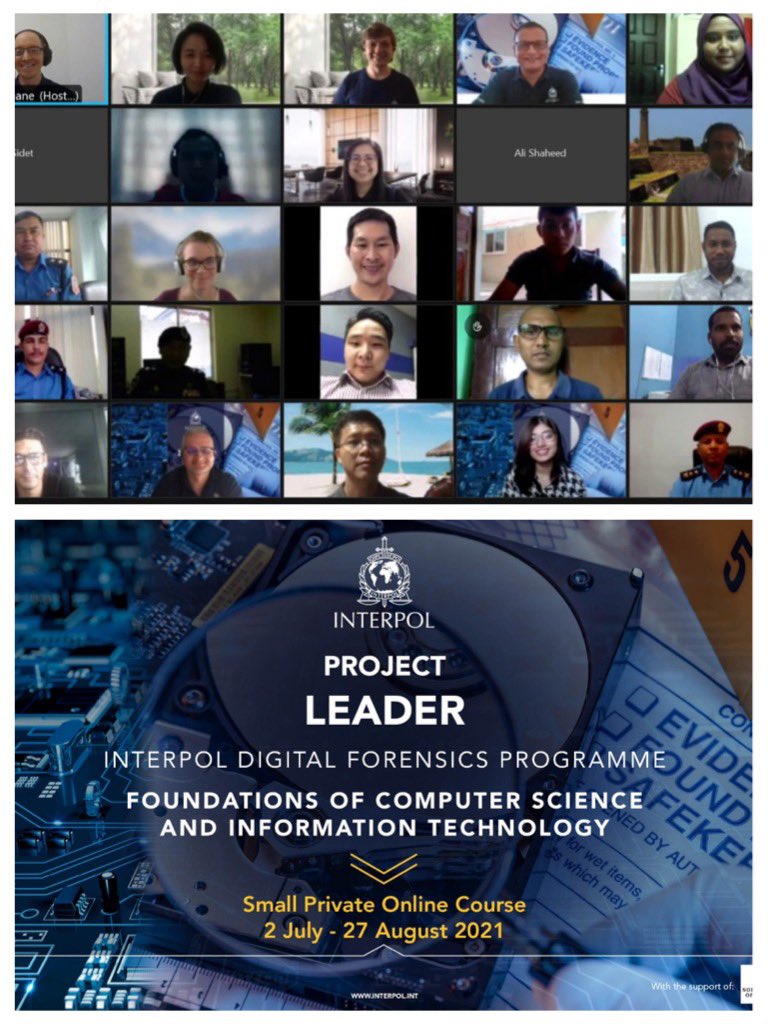
Project LEADER concludes its 8-week training course: Foundations of Computer Science& Info Technology. Covering aspects of forensic analysis of digital devices to enhance #DigitalForensics #Capabilities Our thanks to instructors @ucddublin & our INTERPOL MC participants. pic.twitter.com/Apo0vrNdZJ — INTERPOL Training (@INTERPOL_CBT) August 27, 2021 I am delighted to say that we (DigitalFIRE) have just completed a…
-
Dr. Pavel Gladyshev speaks about digital forensics on Channel News Asia
Last week DFIRE participated in Inteprol World 2019 in Singapore. It was a great event with a truly global reach focusing on connecting international police forces for a safe World, and promoting enchanted cooperation between law enforcement, academia, and private sector. Unlike the previous Interpol World 2017, the bulk of discussion was organised into so-called…
-
DFIRE Forensic Prolog
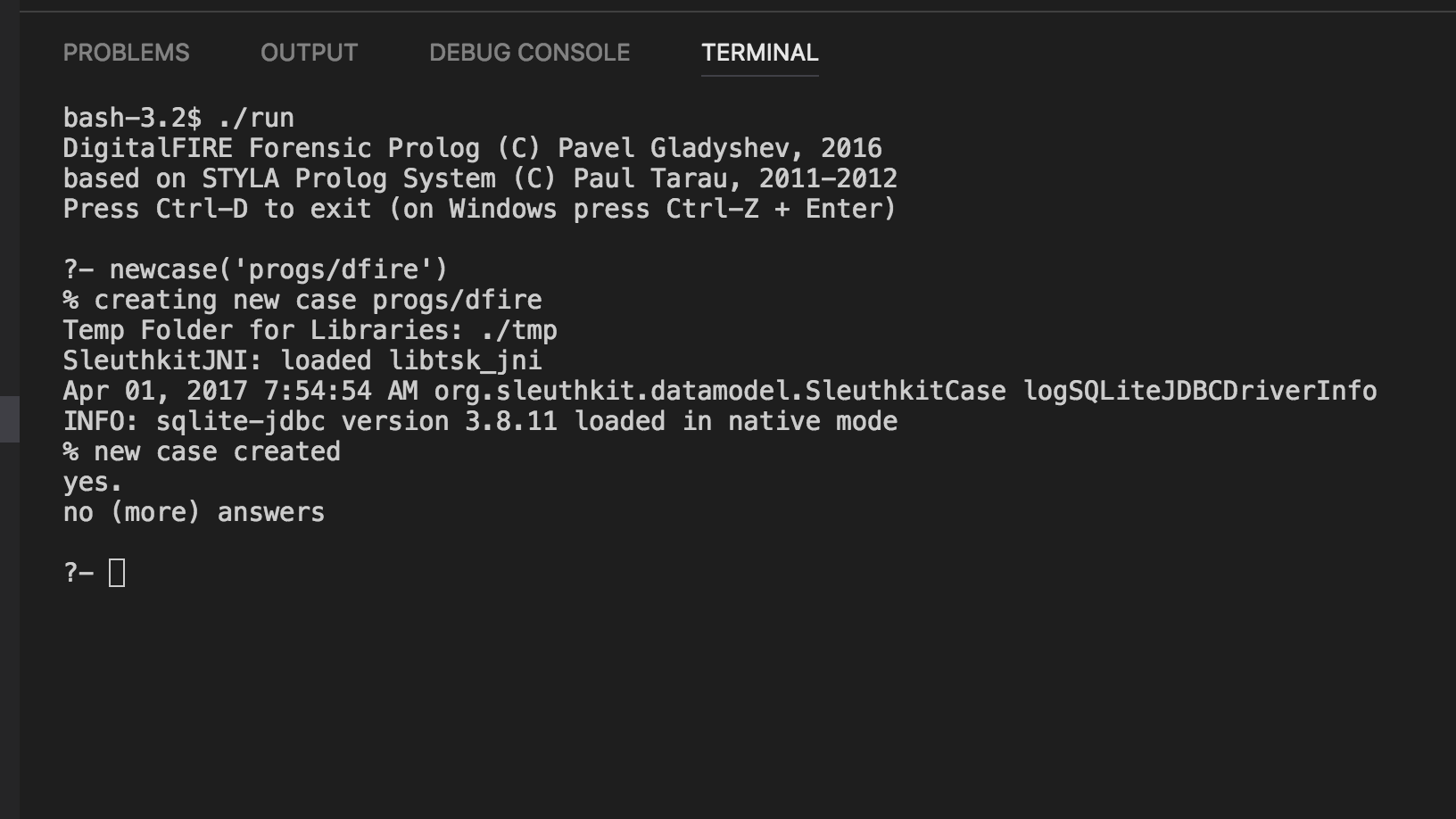
Introduction Digital forensic examiners rely on software tools to analyze digital evidence and answer investigative questions. Although the ability to create custom software is not required in every investigation, it is important to be able to automate repetitive processing tasks. A variety of general-purpose programming languages is used for that purpose ranging from C and Bash scripting,…
-
Ethical Hacking Workshop

The workshop is delivered jointly by the IBM Ethical Hacking team (IBM Ireland) and UCD MSc Digital Investigation and Forensic Computing team on Wednesday 25 January 2017.