Author: Joshua I. James
-

DigitalFIRE Mutual Legal Assistance Study
Please help DigitalFIRE Labs understand the current state of Mutual Legal Assistance Requests relating to digital evidence, and be entered for a chance to win a FIREBrick write-blocker or an Amazon gift card. The survey on Mutual Legal Assistance Requests Concerning Digital Evidence can be found here: http://goo.gl/gnrJtN This survey has been commissioned by the United Nations Office…
-

An Argument for Assumed Extra-territorial Consent During Cybercrime Investigations
During cybercrime investigations it’s common to find that a suspect has used technology in a country outside of the territorial jurisdiction of Law Enforcement investigating the case. The suspects themselves may also be located outside of the territory of the investigating group. A country may be able to claim jurisdiction over a suspect or device…
-

Challenges with Automation in Digital Forensic Investigations
Abstract The use of automation in digital forensic investigations is not only a technological issue, but also has political and social implications. This work discusses some challenges with the implementation and acceptance of automation in digital forensic investigation, and possible implications for current digital forensic investigators. Current attitudes towards the use of automation in digital forensic investigations are examined, as…
-
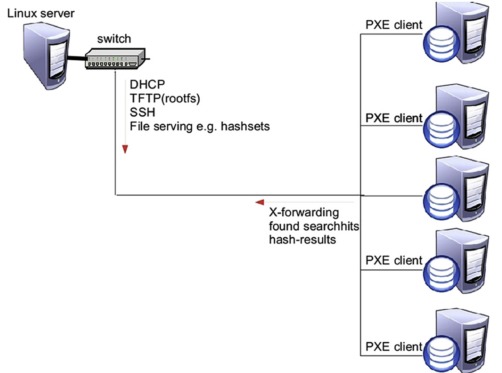
Automated Network Traige
In many police investigations today, computer systems are somehow involved. The number and capacity of computer systems needing to be seized and examined is increasing, and in some cases it may be necessary to quickly find a single computer system within a large number of computers in a network. To investigate potential evidence from a…
-
What is Cybersecurity?
Last week, a number of Korean organizations fell victim to cyber attacks. This has prompted discussions about cybersecurity in Korea, and while following this issue I’ve realized that Korea’s main challenge appears to be understanding what cybersecurity actually is. From many of the discussions, representatives from various organizations appear to believe that security is a…
-
Legal Protest and Distributed Denial of Service
The United States government, via the “We the People” portal (petitions.whitehouse.gov), was petitioned by Dylan K. [1] to “Make, distributed denial-of-service (DDoS), a legal form of protest”. The petition states that: With the advance in [Internet technology], comes new grounds for protesting. Distributed denial-of-service (DDoS), is not any form of hacking in any way. It…
-

Digital Forensic Investigation and Cloud Computing
Earlier this year, researchers from the Digital Forensic Investigation Research Group had a chapter published in the book “Cybercrime and Cloud Forensics: Applications for Investigation Processes“. There were contributions from authors discussing practical as well as theoretical aspects of digital crime, investigation, side channel attacks, law, international cooperation, and the future of crime and Cloud…
-

Signature Based Detection of User Events for Post-Mortem Forensic Analysis
The concept of signatures is used in many fields, normally for the detection of some sort of pattern. For example, antivirus and network intrusion detection systems sometimes implement signature matching to attempt to differentiate legitimate code or network traffic from malicious data. The principle of these systems that that within a given set of data, malicious data…
-
Automata Intersection to Test Possibility of Statements in Investigations
When conducting an investigation, many statements are given by witnesses and suspects. A “witness” could be considered as anything that provides information about the occurrence of an event. While a witness may traditionally be a human, a digital device – such as a computer or cell phone – could also help to provide information about…
-
Report of digital forensic standards, processes and accuracy measurement
From December 7th 2010 to December 12th 2010 a survey on Digital Investigation Process and Accuracy was conducted in an attempt to determine the current state of digital investigations, the process of examination (examination phases), and how those examinations are being verified as accurate. An online survey was created in English, and consisted of 10…
-
Survey of Evidence and Forensic Tool Usage in Digital Investigations
This work is in regards to a 2009 project about research into real-world digital forensic practices for the development of highly automated tools to increase speed and efficiency of forensic investigations. A survey was conducted of 30 Law Enforcement officers from different countries in Europe (with 10 respondents). The key findings of the survey are given,…